Compliance
Breaking down HIPAA breaches: What they are and how to avoid them
Estimated reading time: 4 minutes
The Healthcare Insurance Portability and Accountability Act (HIPAA) rules are written in black and white, but in real life, things can be more grey. And HIPAA breaches are no exception. It can be tough to know what counts as a breach and what doesn’t.
What if you’re talking to a colleague and let a client’s name slip? What happens if a client overhears part of a therapy session while walking past an office? Are those considered reportable breaches?
Actually, they aren’t. We’ll explain why later in this post. We’ll also cover common types of breaches, what to do if there is a breach in your practice, the possible consequences of a breach, and how to avoid one.
By the time you’re finished reading, you’ll have a solid understanding of HIPAA breaches and what to do about them.
|
Table of Contents |
What is a HIPAA breach?
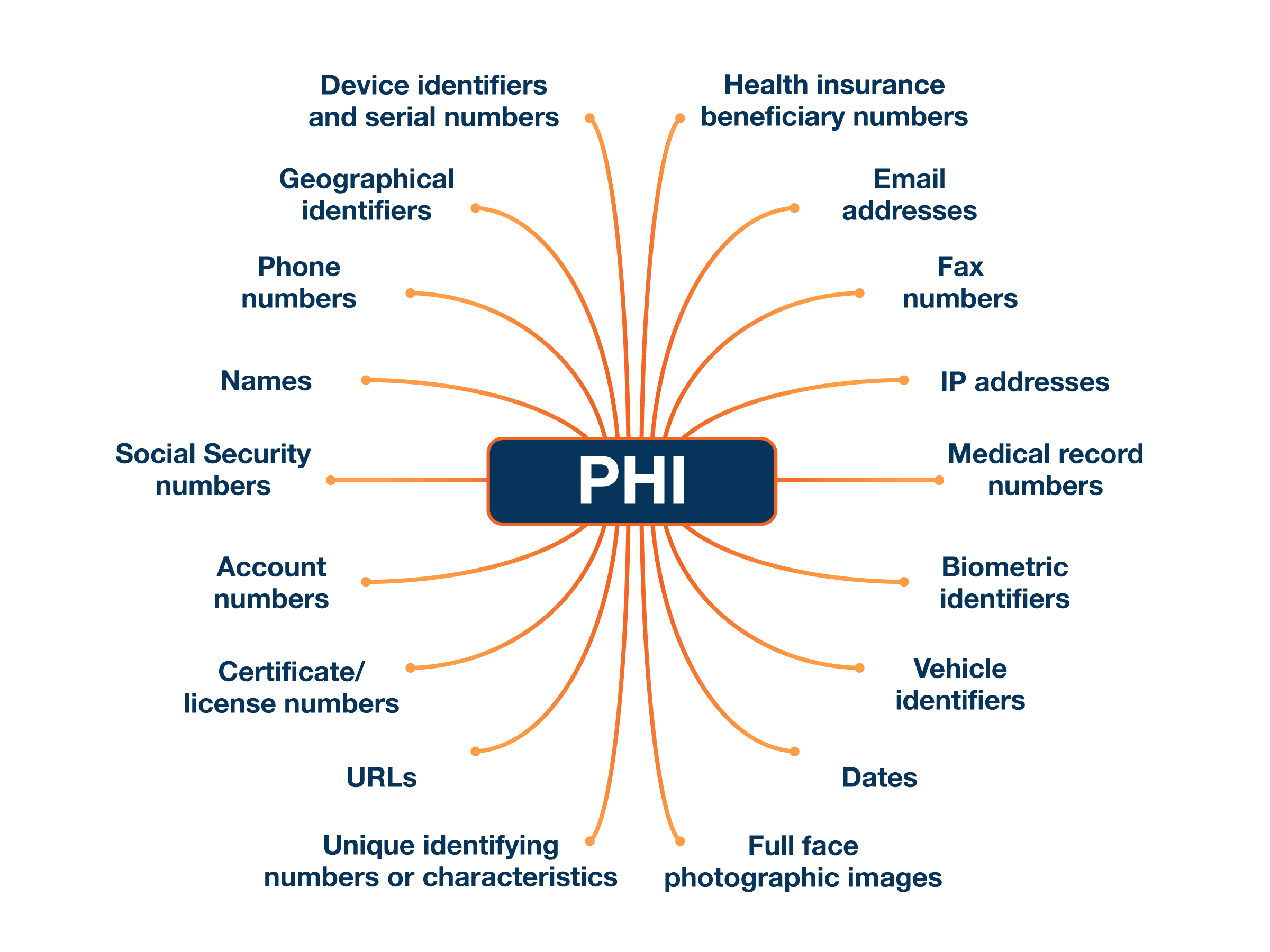
A HIPAA breach happens when protected health information (PHI) is shared with someone who is not authorized to see or use it, according to the Privacy Rule. Or, if you check the U.S. Department of Health and Human Services (HHS) website, you’ll see a breach defined as “an impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of the protected health information.”
|
PHI Information that relates to:
|
What does that mean? Let’s take a look at who is allowed to access and use PHI according to the Privacy Rule. The rule states that covered entities (e.g., healthcare providers) and business associates (e.g., third-party service providers that access and store client data) can only share client PHI with:
- The client or patient being treated
- Organizations involved with the client’s treatment, payment for healthcare services, or healthcare operations (e.g., email providers, insurance services, etc.)
- State or federal governments (according to law)
- Public health authorities, organizations, or individuals regarding public health activities
- Those involved in special circumstances such as health oversight, judicial proceedings, workers’ compensation, research, etc.
If information is shared with anyone else without a client’s written consent, it’s considered a breach. Are all breaches reportable? No, there are some exceptions to this definition that we’ll discuss in the next section.
Breaches only involve unsecured PHI
It’s also important to note that the Breach Notification Rule only applies to unsecured PHI. That means PHI that can be used and/or read. If someone accesses PHI that is unusable, unreadable, or indecipherable, then it isn’t considered a breach.
What makes information unusable, unreadable, or indecipherable?
Encryption makes digital information unusable, unreadable, or indecipherable to unauthorized parties. To meet HIPAA standards, encryption must follow National Institute of Standards and Technology (NIST) guidelines.
For example, if you use Hushmail and an encrypted email is intercepted, it likely wouldn’t be considered a breach. This is because our gold-standard encryption is HIPAA-compliant, making it very difficult for a third party to access the information.
To make physical records unusable, unreadable, or indecipherable, they need to be destroyed. Printed documents, film, or other hard-copy records must be properly disposed of—such as by shredding—to ensure they cannot be reconstructed or read.
So, if someone were to rummage through your recycling bin, it wouldn’t be a breach as long as all documents containing PHI had already been shredded.
|
👉 How to make PHI unusable, unreadable, or indecipherable
|
HIPAA breach exceptions
There are three main exceptions to the HIPAA breach definition. Information shared in one of these three ways isn’t considered a reportable breach.
Exception #1
A staff member (or someone acting under the direction) of a covered entity or business associate acquires, accesses, or uses PHI unintentionally. This counts as an exception as long as they came in contact with the PHI in good faith and within the scope of their role.
Example: A colleague accidentally opens the wrong hard copy file and sees the PHI of one of your clients.
Here, the colleague did not mean to access the PHI and was acting in good faith. The HHS makes this exception since your colleague is also bound by the Privacy Rule and can’t use or disclose the PHI inappropriately.
Exception #2
A staff member of a covered entity or business associate discloses PHI to another staff member in the same organization or within an organized healthcare arrangement, and both people are authorized to access the information.
Example: You accidentally share a client’s name when talking to a colleague in the same practice.
Remember this example from the beginning of the article? It doesn’t count as a reportable breach because it falls under this exception. And similar to Exception #1, the information stays safe because your colleague must also follow the Privacy Rule.
Exception #3
A staff member of a covered entity or business associate shares information with someone who isn’t authorized to see or use it, but they have good reason to believe it won’t be retained.
Example: You are ready to leave the office when you notice a client sign-in sheet on the reception desk. You are about to put it away when a cleaning employee walks by the desk and glances at the sheet.
Although the cleaner is not authorized to see the PHI, you have good reason to believe they won’t retain the information.
The HIPAA rule on incidental disclosures
The Privacy Rule also makes allowances for something called “incidental uses and disclosures.” These are mini-disclosures that can happen when you work in healthcare but are unavoidable and unlikely to cause any significant harm.
An event is an incidental disclosure if:

- Secondary: It happens as the result of another disclosure allowed by the Privacy Rule.
- Unavoidable: There’s no way to prevent it.
- Limited: Only small amounts of information are revealed.
Let’s take a look at one of the examples we gave at the beginning of this article. If a client walks past an office and overhears parts of a therapy session, it isn’t considered a breach because it meets the criteria of an incidental disclosure.
- It’s secondary. The information the client hears in the hallway results from an allowed disclosure (a client talking to their therapist).
- It also couldn’t be avoided. Even though the door is closed and the room is sound-proofed, there’s nothing else the practice can do to ensure voices aren’t heard from the hallway.
- It’s limited. The client in the hallway can’t hear the whole conversation and doesn’t know the name of the client in the room.
Even though there are allowances for incidental disclosures, you should always do your best to keep PHI safe in your practice.
|
👉 Tips to keep PHI safe
|
Common types of HIPAA breaches
Breaches can happen wherever PHI is stored or used. The OCR breach report categorizes breaches as follows:
- Hacking/IT incidents
- Unauthorized access/disclosure
- Theft/loss
- Improper disposal
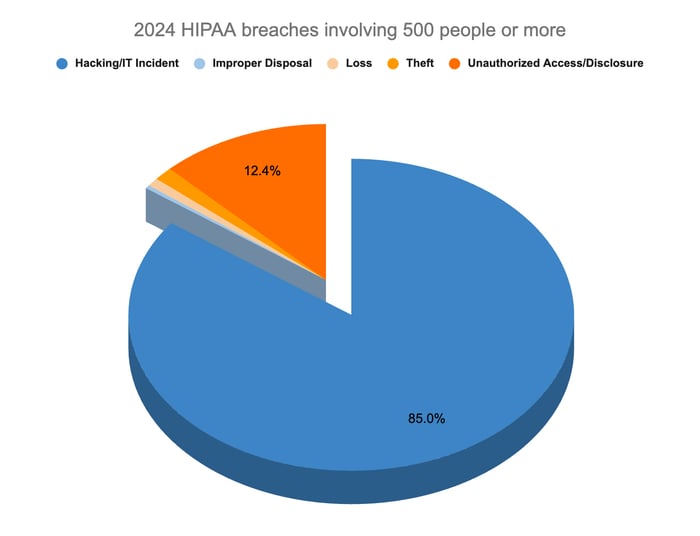
Hacking/IT incidents
According to the OCR breach report, this was the most common type of HIPAA breach in 2024, accounting for 85% of breaches involving 500 people or more.
This category involves events like third parties hacking into network servers or phishing attacks. Since so much information is stored on computers and online, these types of breaches often affect more people than other violations.
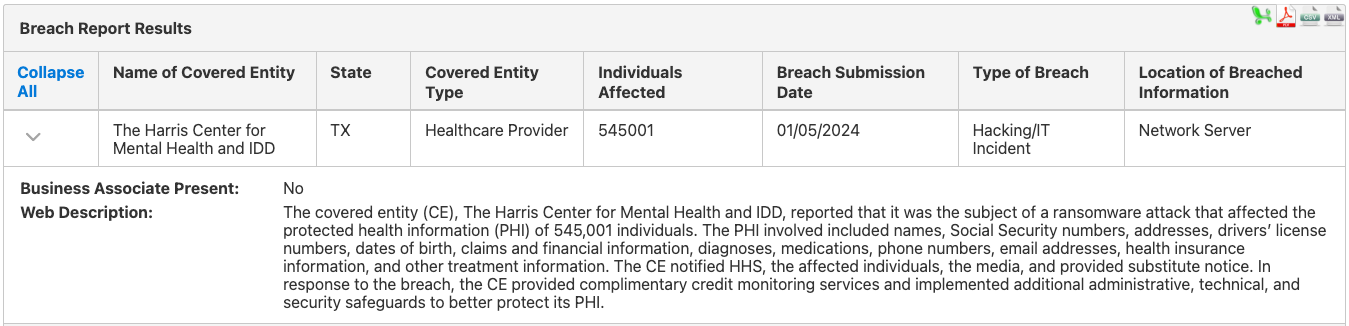
For example, on January 5, 2024, The Harris Center for Mental Health and IDD in Texas reported it was the subject of a ransomware attack. Over 500,000 people were affected. The breached information included names, dates of birth, diagnoses, addresses, and insurance information.
Since these kinds of breaches are so common, it’s critical to do everything you can to keep your computers and email secure. If you have staff, be sure to train them on protecting e-PHI.
Unauthorized access/disclosure
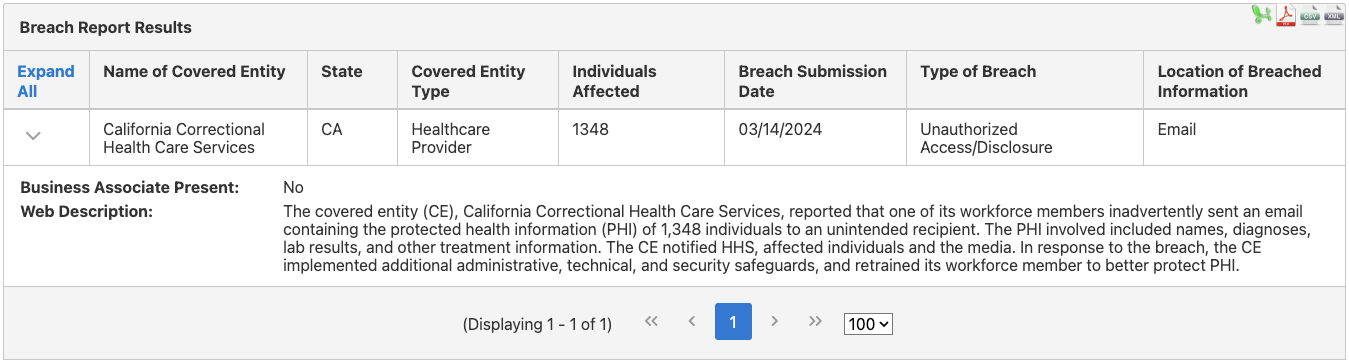
This was the second most frequent type of breach in 2024. These violations are the result of PHI being seen or used by people who don’t have the authority to access it. In many cases, staff members sent information to the wrong people unintentionally.
When a staff member of California Correctional Healthcare Services accidentally emailed the wrong person, the PHI of over 1,000 people was compromised. The information included names, diagnoses, and lab results.
Theft/Loss
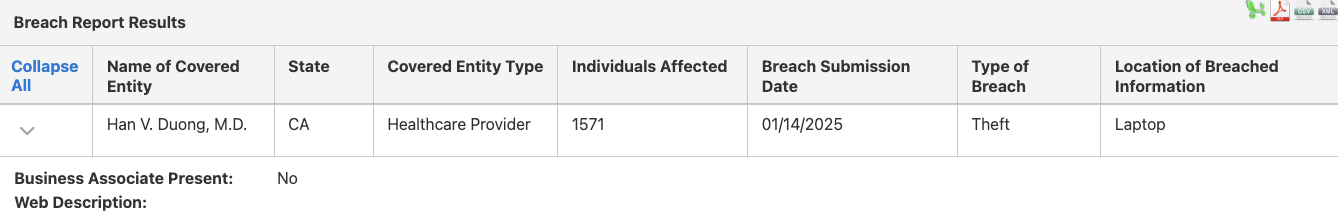
Although these breaches are less common, they do happen. Laptops, desktop computers, papers, films, and even medical equipment that contains PHI can be stolen or lost.
In January 2025, it was reported that Han V. Duong MD’s laptop was stolen. Since it contained the PHI of 1,571 individuals, an OCR investigation into the incident was opened.
Improper disposal
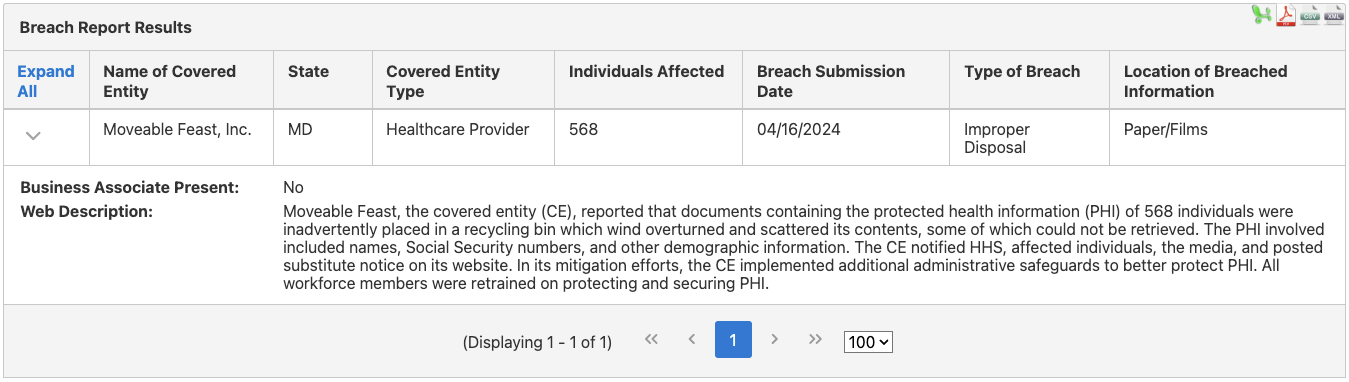
This was the least common type of breach in 2024, with only 4 cases in that year. Improper disposal relates to PHI that hasn’t been destroyed according to the HIPAA Privacy and Security rules or PHI that has been stored in a facility that isn’t secure.
In 2024, for example, employees of Moveable Feast Inc. in Maryland put documents with PHI in an outdoor recycling bin that was tipped over by the wind. The documents were scattered, and some couldn’t be retrieved. Over 500 people were affected.
What to do if there is a HIPAA breach in your practice
Having a breach, especially a large one, can be a nightmare for a small practice. But there are things you can do to deal with the issue and prevent more breaches.
Here are some steps to take if you experience a breach.
Step 1: Don’t panic.
Step 2: Go over your policies and procedures on how to deal with breaches.
Don’t have these? Write some before a breach happens!
Step 3: Note all the relevant details, including:
- The date you discovered the breach
- How you found out about it
- Steps you took to resolve the problem or stop further breaches
Step 4: Notify all clients affected by the breach.
These notifications should be put in writing and either emailed or mailed to the clients involved. To be allowed to email the notification, the individual must have agreed to receive notifications electronically, so obtain the consent when the person first becomes a client.
If you don’t have current addresses for more than 10 clients, you must post the information on the homepage of your website for at least 90 days or inform local media. Be sure to include a toll-free phone number that clients can use to contact you.
If the breach involved e-PHI, you should also:
- Disconnect all devices from the internet by unplugging from your firewall(s) or router(s) until the location of the breach has been determined.
- Disable (but don’t delete) any remote access and wireless access points.
- Change all account passwords, including for any accounts used to manage your practice, and disable (don’t delete) accounts that aren’t critical.
- Switch to your backup secure form of communication that you hopefully included in your policies and procedures.
|
If the breach affects fewer than 500 people, you must report it to the HHS by the end of the year and no later than 60 days after the end of the year.
If it involves 500 people or more, you must report it to the HHS immediately (and no more than 60 days after the breach is discovered) and inform prominent media outlets in your area.
The consequences of a HIPAA breach
HIPAA breaches can lead to serious consequences, including investigations and oversight by the OCR, fines, or even criminal charges.
Investigations can be nerve-wracking and time-consuming. The OCR will request access to your policies and procedures or other documents. You may also need to hire a lawyer to guide you through the process.
Breaches can also be embarrassing and may lead to a loss of reputation. Large breaches (affecting 500+ people) are posted publicly on the HIPAA Wall of Shame (the OCR breach report) and must be announced to local media. This can damage client trust and could make it harder to find and retain clients.
If the OCR finds that the breach was caused by a HIPAA violation, you may be ordered to take corrective actions to ensure a similar breach doesn’t happen again. Your practice could be monitored by the OCR for up to three years. If the case involves willful neglect of the rules or intentional misuse of PHI, you could face fines or even criminal prosecution.
Run a secure practice to avoid breaching HIPAA

Keeping your clients’ private information safe is an important responsibility. Although it may not be possible to avoid a breach, doing your best to prevent one shows the HHS that you care about compliance. It could also help to prevent serious problems down the road.
|
Make HIPAA compliance a regular part of the day-to-day operations of your practice. You can do this by:
- Completing HIPAA training
- Subscribing to the HHS listserv to receive emails from the HHS about privacy, security FAQs, guidance, and technical assistance materials
- Writing policies and procedures to protect client data (and training any staff you may have on them)
- Including plans for what to do if PHI is lost, stolen, or shared accidentally
- Having an Incident Response Plan that outlines what you will do if your computer systems are affected and e-PHI is breached
- Conducting a regular risk assessment (at least once every year) to make sure you’re doing everything you can to protect client data
- Putting a Business Associate Agreement (BAA) in place with any companies you work with that have access to client data and store it
- Training staff (if you have them) on how to protect client information
- Using encrypted email with a reputable provider like Hushmail 😉
Your email isn’t going to encrypt itself!
Overwhelmed by the business side of private practice? In this guide, therapists share 20 ways they've offloaded what drains them, to create more space for the work they love.