Compliance
What is the HIPAA Wall of Shame (and how to avoid it)

Your clients trust you with their private medical information.
Unfortunately, security breaches are on the rise.
Over 49 million healthcare records were breached in 2022, more than any previous year except 2015.
If you suffer a breach that affects 500 or more individuals, you will face an investigation and appear on the HIPAA Wall of Shame.
This could result in heavy fines, loss of trust, and a corrective action plan (more on this later...).
The scary thing is ending up on the wall is possible, even for small practices.
For example, imagine you've been keeping records for six years, which is the minimum HIPAA requires. Adding 8 new clients per month over this time period would mean you have enough records to potentially impact over 500 individuals if you suffered a breach.
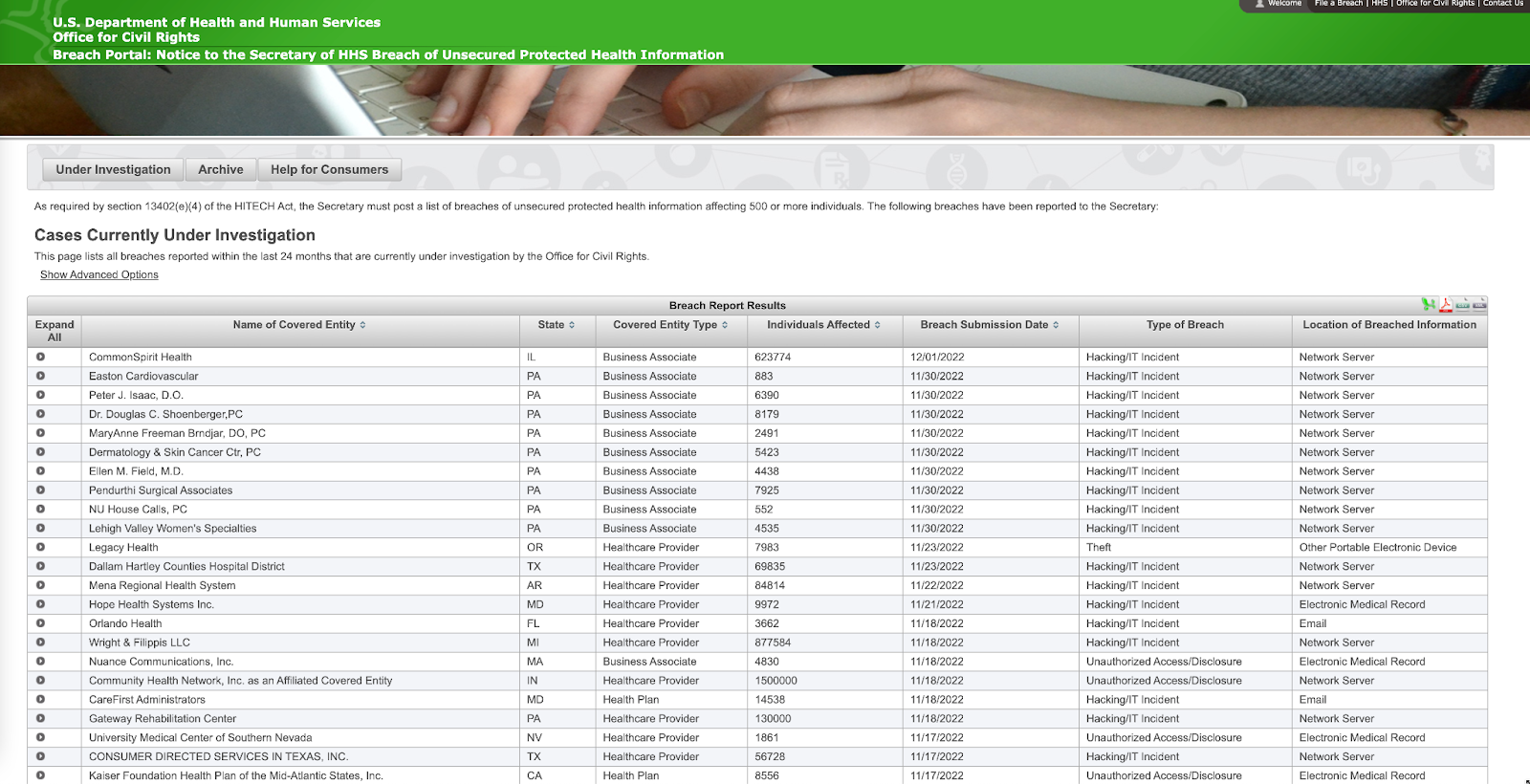 The HIPAA Wall of Shame, where security breaches are listed publicly for two years
The HIPAA Wall of Shame, where security breaches are listed publicly for two years
So, how can you avoid being a HIPAA Wall of Shame statistic and keep your records secure?
Most of the work comes down to how well you comply with HIPAA laws and being smart about your practice's communication methods. Small changes, like securing your emails and knowing how to spot an attempt to access your records without authorization, can save your practice from landing in hot water.
This guide will help you stay compliant and off the HIPAA Wall of Shame.
Let’s dive in.
|
Table of Contents |
Everything you need to know about the HIPAA Wall of Shame
The HIPAA Wall of Shame is a public listing that provides information about breaches affecting 500 or more individuals. This page lists all breaches reported within the last 24 months that are currently under investigation.
It was created to inform the public about failures in protecting client data.
All it takes is an email hacker or security failure for you to suffer a breach. Just take a look at some of the most common HIPAA breaches:
- Stolen/lost laptops and electronic devices
- Computer hacking and viruses
- Improper access to records by practitioners or receptionists
- Unsecure/unsafe digital and paper records
- Releasing client information (intentionally or unintentionally) to the public
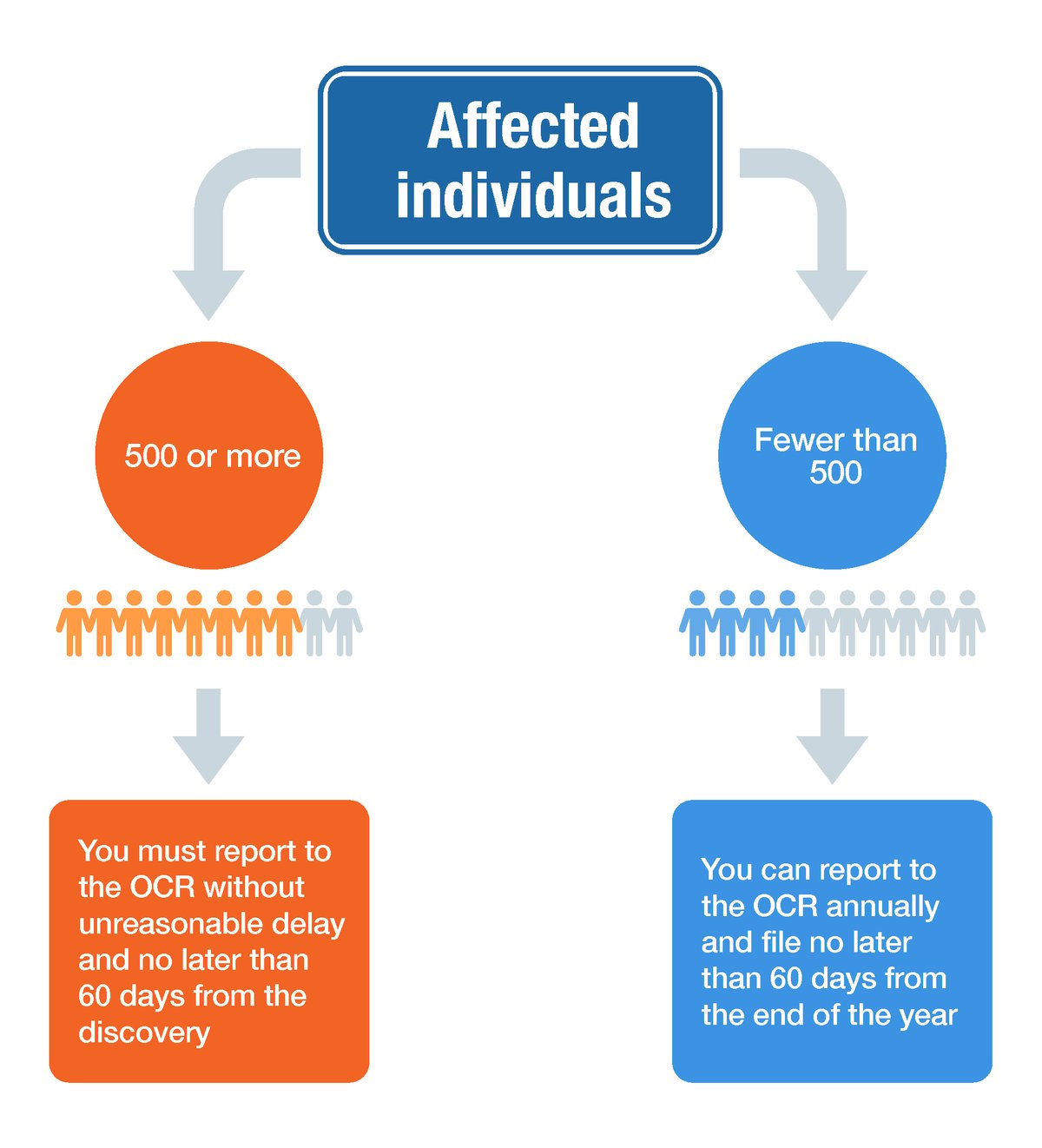
No matter how the breach happens, if client records have been compromised, you must investigate and report to the affected individuals without unreasonable delay and no later than 60 days from the discovery.
|
What is the OCR? The Office for Civil Rights (OCR) is the agency within the U.S. Department of Health and Human Services that investigates reported breaches and failures to protect health information. |
What patient information are you legally required to protect to avoid a HIPAA breach?
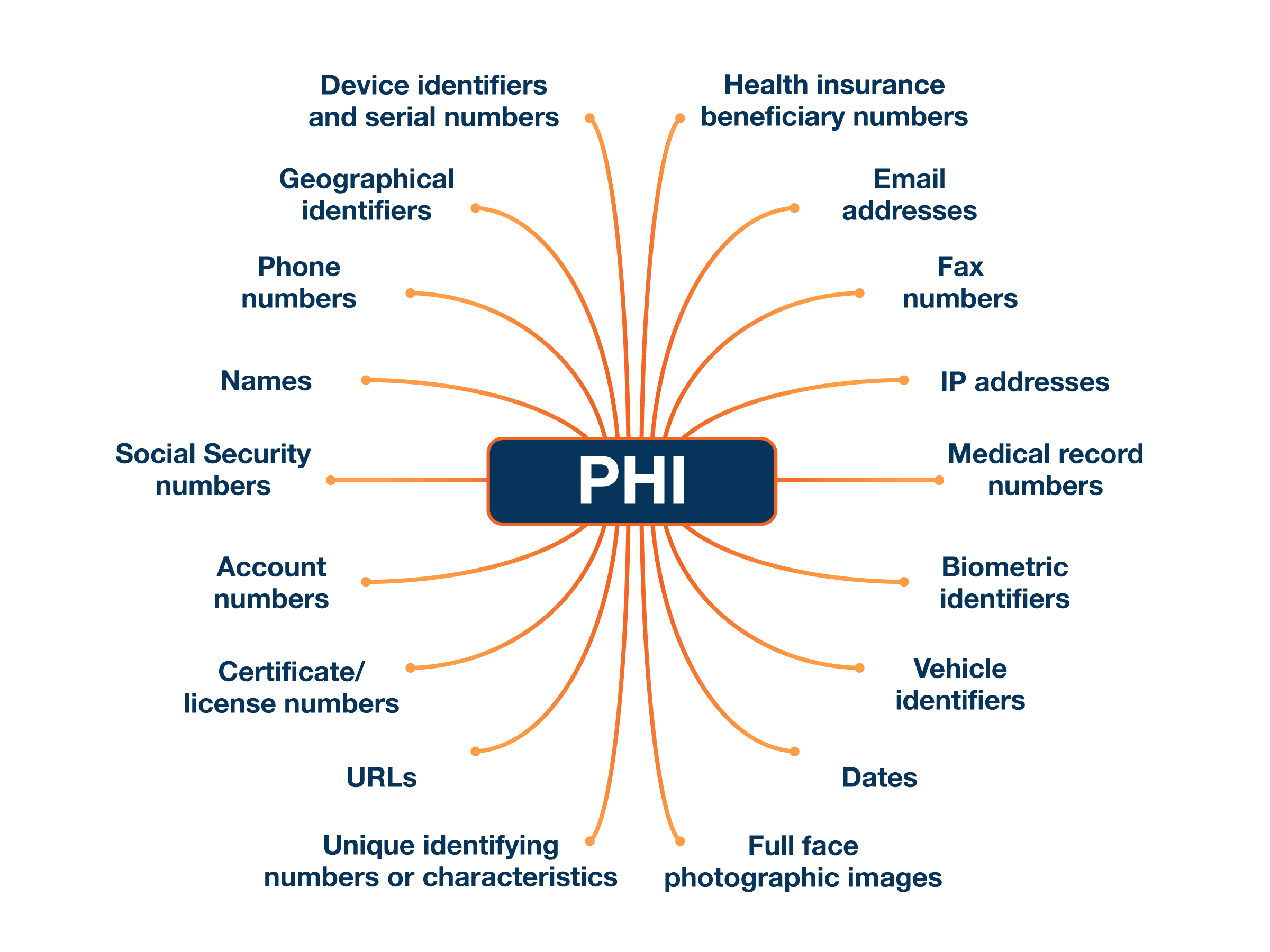
Under the law, healthcare practices must keep protected health information (“PHI”) safe.
|
What is Protected Health Information (PHI)? PHI is information that relates to:
|
Any information that could identify one of your clients (as below) constitutes PHI:
Here’s the bad news. No magic combination of security measures will completely protect your practice. But there are ways to minimize the chances of this happening (which we will get to soon!).
And if there is a breach, your compliance is one factor determining the severity of the penalties.
First, let's talk about why you should do everything possible to avoid ending up on the HIPAA Wall of Shame.
What are the consequences of being on the HIPAA Wall of Shame?
Your practice being publicly listed on the HIPAA Wall of Shame is more than just an embarrassment.
If 500 or more individuals are affected:
- Your practice will be placed on the HIPAA Wall of Shame for two years
- You could face fines of up to $50,000 per violation (depending on the seriousness of the breach). These fines can reach $1.5 million if security breaches aren’t fixed
- Your clients (and future clients) will potentially lose trust, which could impact your business for years
- Your practice may have to enter a corrective action plan and be subject to OCR oversight for one to three years which is potentially even costlier.
Although these consequences are harsh, there are some exceptions to a breach of client information that can save you from landing on the Wall of Shame.
The four exceptions to a HIPAA breach
Not every HIPAA breach is serious enough that it ends with your practice on the Wall of Shame, which is why HHS has carved out some exceptions.
Before you disclose a HIPAA breach, check if it falls under one of the four exceptions:
1. If a person unintentionally acquires or accesses client records and protected information, but it's within their scope of authority, you don't have to disclose the breach. Example: a receptionist accidentally opens the wrong client file when booking an appointment
2. If a person accesses client records and accidentally discloses information to another person who is authorized to access records, it's not considered a breach. Example: a receptionist gives a therapist records for the wrong client when they come for their appointment.
3. When an employee or contractor discloses information to someone, but they believe the person wouldn't retain it. Example: a practitioner accidentally gives a client a receipt with another patient’s information on it (but quickly grabs it back before they can read it).
4. If someone has attempted to access client information, but they haven’t been able to access it because it’s encrypted. Example: a receptionist accidentally sent a secure email to the wrong client.
Unfortunately, if a breach doesn't fit into one of the exceptions, a practice will usually be published on the Wall of Shame and hit with a fine. Let's look at how one healthcare organization ended up on the HIPAA Wall of Shame—and what you can learn from their mistakes.
Lessons from a serious breach that landed a practice on the HIPAA Wall of Shame
Not all HIPAA breaches look the same, but once they happen, a practice must take steps to ensure clients are protected.
Let's look at a recent incident and figure out what went wrong so you don't make the same mistake. In 2022, Jackson-based Mississippi Sports Medicine and Orthopaedic Center fell victim to a data breach that affected 500 patients.
It was discovered that an unauthorized individual had access to the Center's computers and employees' email accounts. As a result, patient records and personal information, such as names, medical histories, and financial information, were compromised.
After the breach was discovered, the Center took steps to secure computers and emails to keep any client records safe. And although the Center did everything right after it discovered the breach, such as reporting it and alerting patients, it did affect 500 patients—landing it a spot on the Wall of Shame.
Biggest takeaways from this HIPAA breach
- You must report a HIPAA breach without unreasonable delay and no later than 60 days after the discovery. In this case, the practice alerted authorities and patients within HIPAA's official deadline, which could decrease the financial penalty given.
- Put policies in place to deal with a HIPAA breach, especially if you have a receptionist or administrator who handles client records. If there is a breach, they’ll know when it needs to be reported, and what steps (like notifying HHS and the media) need to be taken inside the 60-day reporting window.
As you can see from this example, ending up on the HIPAA Wall of Shame isn't always something that just happens to large practices with thousands of clients. It can happen to any practice with over 500 client records.
If you are involved in a HIPAA breach, there are steps you can take to minimize the risk and financial penalties to your practice 👇
What to do if you’re involved in a HIPAA breach
When it comes to HIPAA breaches, you don’t need us to tell you that prevention is better than a cure.
But if you do fall victim to one, there are some steps you need to take immediately to avoid huge fines and damage to your reputation.
Step 1. Investigate whether or not you have actually experienced a HIPAA breach
If you think client data has been compromised, do some simple checks to see if there is actually a breach and, if so, what the reporting requirement is.
To do this, look at:
1. What information was involved in the breach and whether or not clients can be identified by it (names, addresses and date of birth are big red flags here)
2. The person who accessed the information without authorization (and if they disclosed it to anyone else)
3. If a client’s health information was actually viewed or acquired by anyone
4. The seriousness of the risk. Was a client’s record accidentally accessed, or has there been a breach of 500 or more client records? (Hint: the larger breach is more serious!)
If you decide there was a breach that needs to be reported, it’s time to start gathering documents.
Step 2. Hand over all necessary information and notify the right departments
HIPAA breaches serious enough to place your practice on the Wall of Shame need to be reported not only to HHS but also to a media outlet. Depending on your state, you may also be required to notify an applicable state agency.
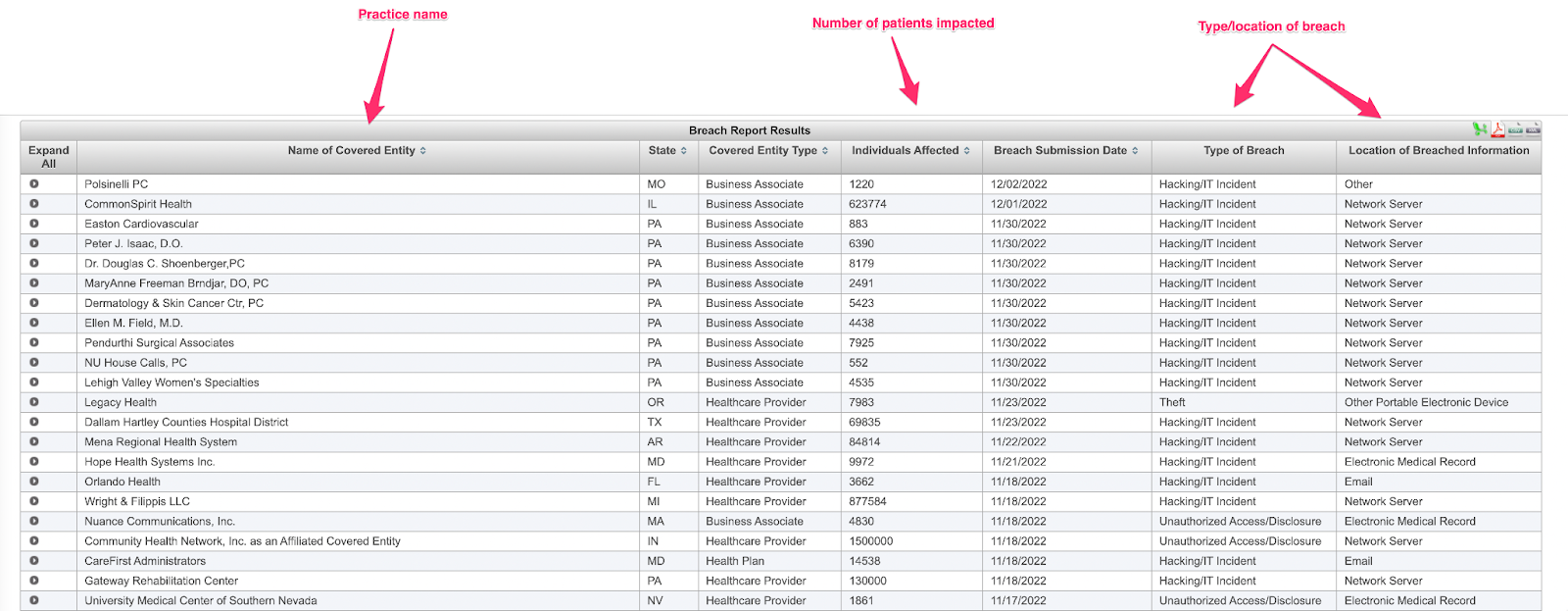
You must report on the HHS website without unreasonable delay and no later than 60 days after the breach. You need to provide details such as:
- Your business/practice name
- What state you operate in
- How many clients have been affected (or possibly impacted) by the security breach
- When you discovered the breach and when it was reported
- The type of breach that occurred. Did a computer get stolen, or did hackers access your records using an email scam?
- What records were impacted and the source or the breach (was your main email hacked, or were paper records stolen?)
This information will then be publicly available on the Wall of Shame, as HHS is required by law to publish the listing:
Once this information is reported to HHS, the next step is telling your clients about the breach.
|
Good to know All HIPAA breaches affecting 500 or more individuals within the last 24 months will appear on the Wall of Shame. However, every breach is archived and can be searched for (and viewed) by the public. |
Step 3. Notify your patients of the HIPAA breach
Do you need to tell your clients? The answer is absolutely yes, and it must happen without unreasonable delay and within 60 days.
Anyone with protected health information accessed or compromised needs to be notified. While you should contact clients you know have had their records accessed, it's also wise to notify any person you think may have been affected.
Victims of the breach should be notified through a letter, which needs to be sent within 60 days to the last known address you have on file. Suppose you don't have up-to-date contact information for 10 (or more) clients. You must either announce the security breach on your website so potential victims are notified and can contact you for more information or notify the local media. A notice can also be emailed if the individual has agreed to receive such notices electronically. Obtaining these authorizations in advance may be a huge timesaver in the event of an actual breach.
What are the financial penalties of a HIPAA breach?
You’ve filed the necessary paperwork and notified your clients. Now, it’s time to think about what penalties you will face.
Penalties are handed out using a tiered system:
| Description | Fine | |
| 1 | Your practice didn't know about the violation and attempted to comply with the rules. |
From $100 to $50,000 for each offense. |
| 2 | Your practice knew about the violation, but it couldn’t have been prevented (think computer hackers or a stolen device.) | From $1,000 to $50,000, and are limited to $100,000 a year. |
| 3 | HIPAA rules were neglected, but your practice tried to correct the mistake within 30 days. | From $10,000 to $50,000 per violation and a maximum of $250,000 a year. |
| 4 | The most serious violation where a healthcare practice willfully neglects HIPAA rules and doesn't try to fix its mistake. |
$50,000 per violation or a maximum of $1.5 million a year. |
These penalties, especially violations for neglect, can have a devastating impact on your practice. The good news is that you can take some simple steps to minimize the chances of being placed on the HIPAA Wall of Shame.
How to avoid a HIPAA breach (and the Wall of Shame)
Tip 1: Train yourself (and anyone with access to client records) to keep all communication safe
Nearly half of all data breaches happen as a result of receiving a “phishing” email.
Phishing is when someone impersonates a person or company to gain access to your computer and possibly patient records and information. It usually happens when the impersonator sends an email with a link that contains a virus. Once the link is clicked, the virus can spread through your practice’s computer system and put your client records at risk.
The hard part is spotting a phishing email. Look at this example:
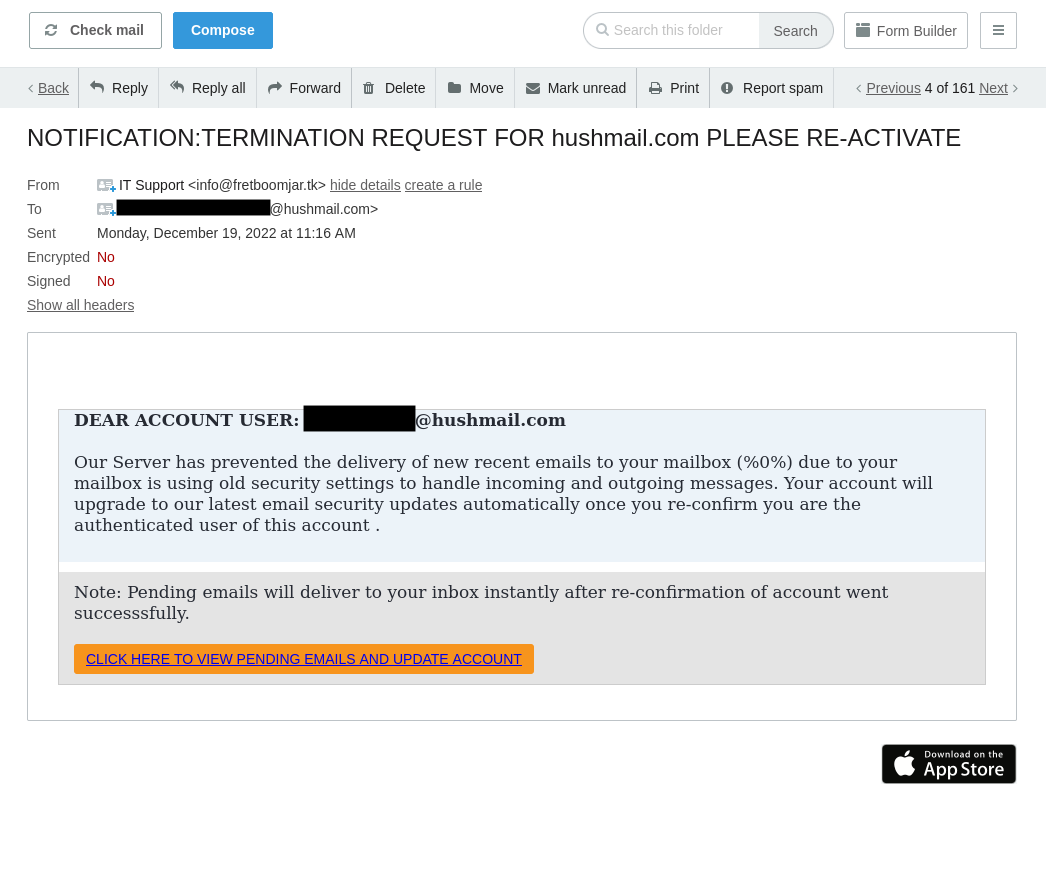 The email appears normal, asking you (or your receptionist) to confirm your account details, right?
The email appears normal, asking you (or your receptionist) to confirm your account details, right?
Look a little closer at the email address. Once it’s expanded, we can see it’s from a fake website:
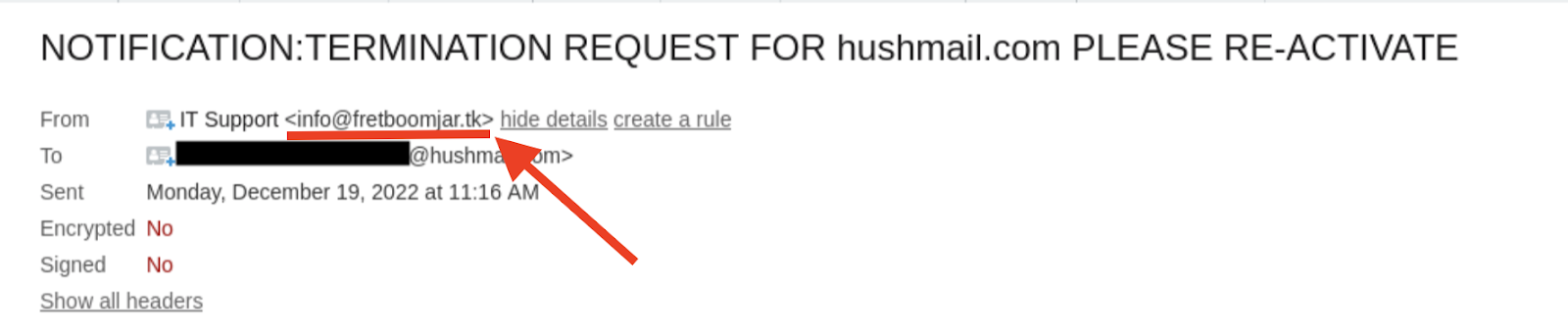
But if you don’t check and click on the link, any information you hand over (or that's stored on your computer) could be at risk. That’s how quickly a phishing attempt can happen. And while other breaches like computer theft made it onto the list, phishing is a bigger problem as you don't know it's happening until it's too late.
So, how can you teach yourself (or your receptionist) to stop it from happening?
Start with staff training. Teach your team how to spot an email imposter and how important it is only to open links or fill out forms when they are sure the sender is legitimate. It's also crucial your team understands how electronic patient records work and how they need to be stored and managed.
Another way to minimize phishing attempts is to use an alias email address for important accounts and contacts.
For example, you may set up alias email addresses for appointments@yourpractice.com and billing@yourpractice.com and then have all messages forwarded to a single admin email address. If someone emails the appointments@yourpractice.com address claiming you have an unpaid bill, you’ll know it's fake because your suppliers use the billing@yourpractice.com address to send any invoices.
Tip 2: Set up two-factor authentication (2FA)
You know how Amazon or Facebook sometimes asks you to prove it's really you and sends you a verification code over text message?
There's a name for that extra bit of security: two-factor authentication (2FA). Unfortunately, a HIPAA breach can be as easy as a hacker guessing your email password and breaking into your inbox, but setting up 2FA can prevent this from happening.
It works because it’s (very) unlikely that someone is trying to hack into your email account to access your account details and your SMS inbox. When you sign in and have the extra verification enabled, there’s a good chance it's actually you.
This level of security for client records and communications can stop outsiders from getting access if they guess an email password or account login. Plus, it's easy to set up.
In Hushmail, for example, go to your account preferences and click the Security tab. The two-step verification setting is located here—click the pencil icon to turn it on:
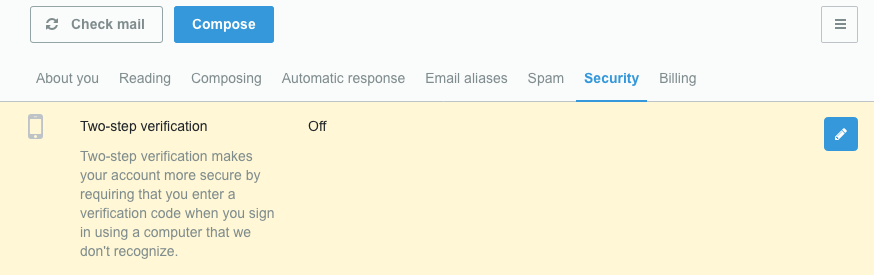
Now, each time you sign into your Hushmail account, you’ll be sent a verification code (either by text message or to another email address) so we know it’s really you.
Tip 3: Minimize the chance of human error with safeguards
You and your team might not be IT gurus. However, you can set up some safety nets on your practice's computer system to minimize the chances that you (or a colleague) will accidentally expose client information.
This exact situation happened at a hospital in Chicago when a temporary worker accessed 682 patient records, including prescriptions and treatment information, without permission. The hospital couldn't find out why the temp worker had accessed the records, and no patient information was disclosed to anyone else.
This incident is a case of unauthorized access to patient data. And as 500 patient records were impacted, the hospital had to notify HHS, media outlets, and, of course, the patients themselves.
Certain safeguards can be put into place to protect you against the risk of human error, like using antivirus software and limiting what records can be accessed inside your electronic health record software. For example, you can restrict a receptionist's access to billing and intake forms while you’ll still have access to full client records and medical histories.
You can't avoid every human error or unauthorized login, but you can minimize them with the right training and restrictions.
|
Pro-tip We’ve created 6 quick tips to ensure your emails are HIPAA compliant. Enter your email to receive them: |
Tip 4: Stay off the HIPAA Wall of Shame with the right tools
An email service that’s already compliant with HIPAA takes the hard work out of ensuring messages between you and your clients are safe.
Using a tool like Hushmail, you can safeguard client communication like emails, forms, and signed documents using added security features. With Hushmail, you can send and receive sensitive information through secure email and forms without using complex software or hiring an IT professional. That's because it looks just like your regular email service:
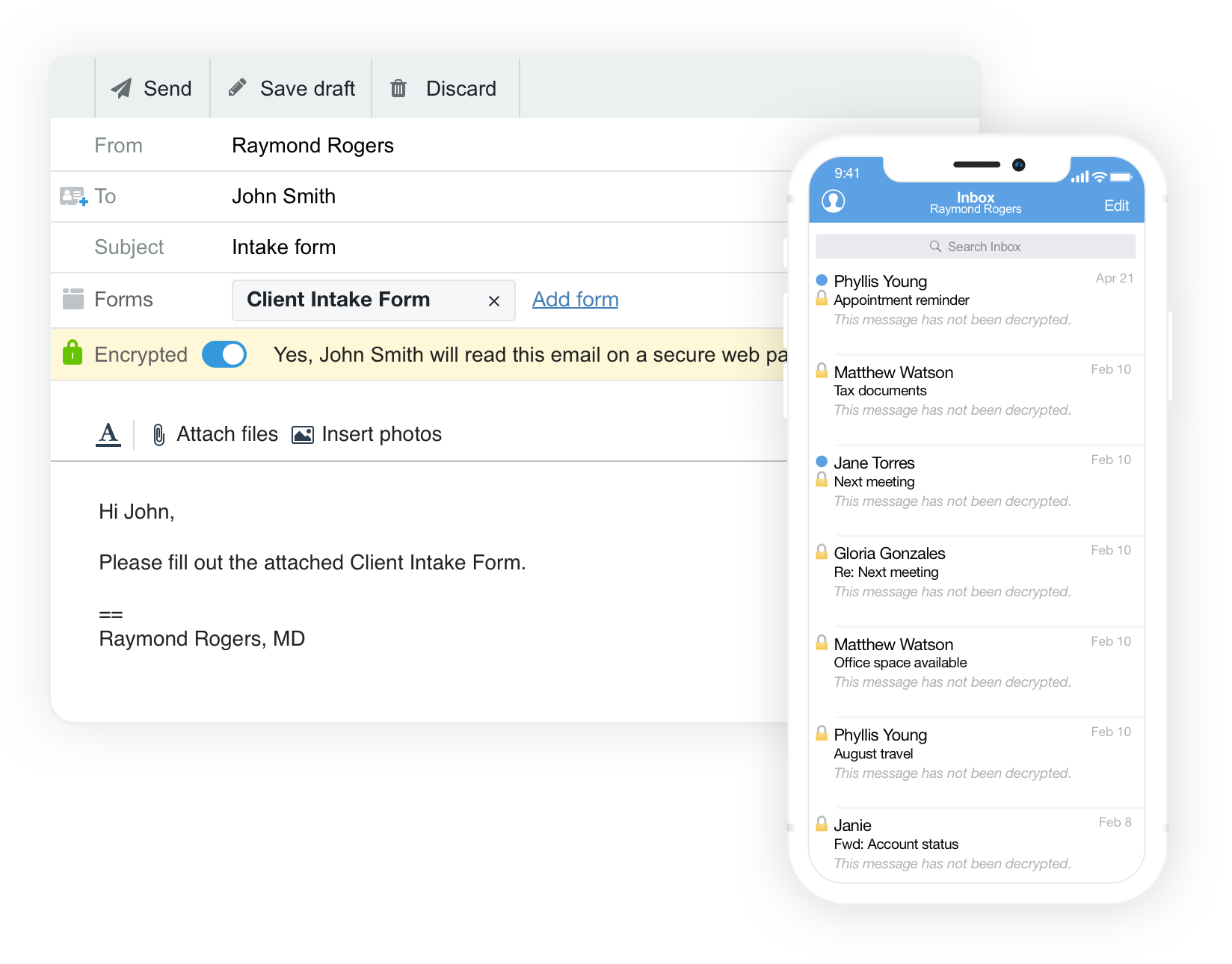
It’s designed for busy healthcare practitioners to handle HIPAA requirements so you can spend time doing what you do best—taking care of your clients.
Find out how you can stay compliant with Hushmail for Healthcare.
Overwhelmed by the business side of private practice? In this guide, therapists share 20 ways they've offloaded what drains them, to create more space for the work they love.




