Compliance
A Simple Guide to Understanding the HIPAA Breach Notification Rule
Estimated reading time: 10 minutes
If you own a small healthcare practice or work in one, you may think a breach won’t happen to you. But the truth is—breaches can happen to anyone. A stolen laptop or a misdirected email could be all it takes.
That’s why it’s essential to understand the HIPAA Breach Notification Rule: what it is, how it works, and what to do if a breach happens in your practice. Having clear policies in place—and following them—is key to staying compliant and protecting your clients.
But wading through the rule’s legal jargon isn’t always easy. This guide breaks it all down for you in plain English.
|
Table of Contents |
What is the HIPAA Breach Notification Rule?
The Breach Notification Rule explains what breaches are and what they aren’t. It also outlines whom to notify in the event of a breach and how.
The rule applies to Covered Entities and Business Associates. Covered Entities include most healthcare providers, and Business Associates are third-party service providers that handle and store protected health information (PHI).
| Covered Entity (CE) | Business Associate (BA) |
|---|---|
| E.g., physician, therapist, optometrist, dentist, chiropractor, physical therapist | E.g., encrypted email provider, accountant, billing service, attorney, telehealth service |
A healthcare provider, healthcare clearinghouse, or a health plan that…
|
A business that…
|
What is considered a HIPAA breach?
A breach happens when unsecured PHI is accessed, used, or shared in a way that's not allowed by the HIPAA Privacy Rule, and puts the security or privacy of that information at risk.
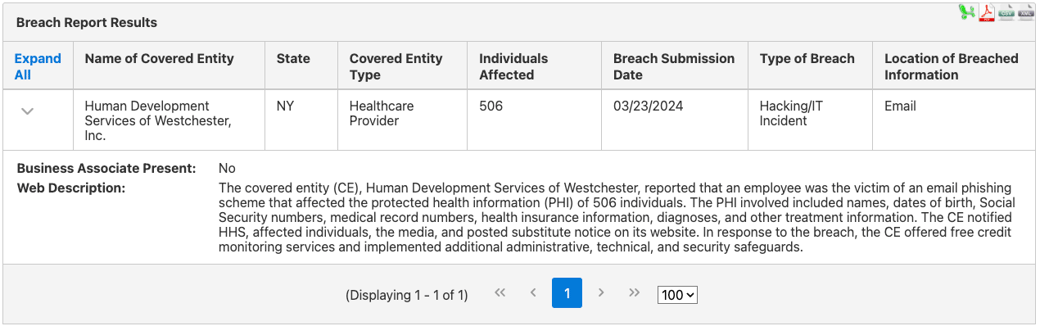
For example, when an employee of Human Development Services of Westchester, Inc. emailed PHI to an unauthorized individual as part of a phishing scam, it caused a breach. The private information of over 500 people was compromised.
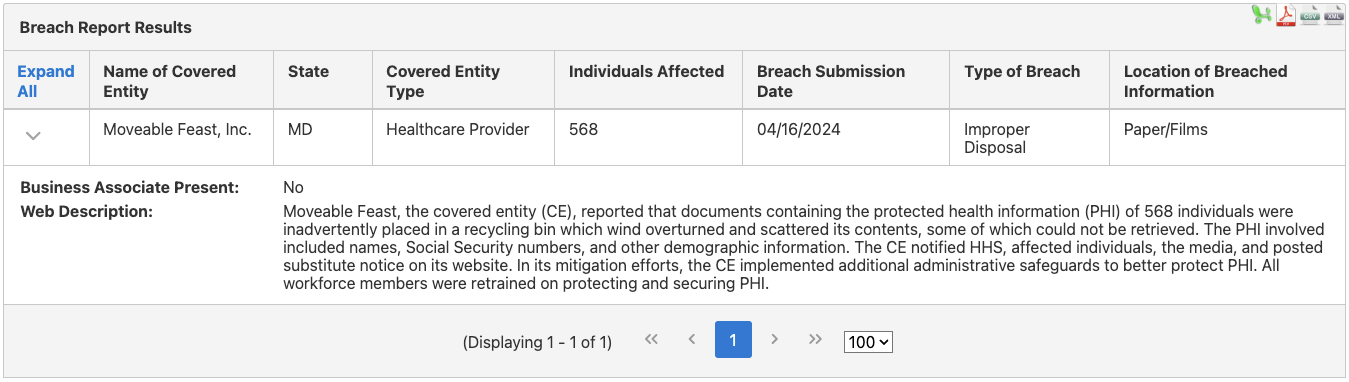
A breach may also involve hard copy information. For example, Moveable Feast Inc. experienced a breach when the wind tipped over an outdoor recycling bin. Many of the documents containing PHI were scattered and couldn’t be retrieved. As a result, information, including names and social security numbers, was put at risk.
| Individual or Organization | Required or Permitted to Disclose Information? | Example |
|---|---|---|
| The patient/client being treated or their legal representative | Required | A client requests treatment records |
| The U.S. Department of Health and Human Services (HHS) | Required during a compliance investigation, review, or enforcement actions | The HHS is investigating your practice and requests records with PHI |
| Organizations involved with treating the patient/client | Permitted | Referring a client to another healthcare provider |
| Organizations involved with payment for healthcare services | Permitted | Sharing PHI with a medical biller |
| Organizations involved in healthcare operations | Permitted for some activities if the organization has a relationship with the patient/client and the information pertains to the relationship | Giving PHI to a health plan for a Health Plan Employer Data and Information Set (HEDIS) |
| Organizations providing public benefit activities | Permitted under certain circumstances | Disclosing PHI to a government authority regarding domestic violence |
Note: The table above is a summary only. For complete information, please visit the HHS website.
What is not considered a breach?
Although the breach definition seems relatively simple, there are some special situations that don’t count as breaches.
Breaches only apply to unsecured PHI
The Breach Notification Rule states that breaches only apply to PHI that is “unsecured,” meaning it’s in a form others can read and use. If the PHI has been secured according to HHS guidelines and a third party accesses it, then it likely wouldn’t be considered a breach.
What are the HHS guidelines? In a nutshell, PHI that’s digital (e-PHI) must be encrypted according to National Institute of Standards and Technology (NIST) recommendations to be considered secure. Hard copy data must be destroyed (e.g., shredded).
For example, if you use encrypted email that meets NIST standards and a third party intercepts one of your messages, it may not be considered a breach. This is because there is a low probability that the third party could get past the encryption to read the information.
Or, if someone accessed the contents of your office recycling bin, it wouldn’t count as a breach if all the documents containing PHI had been shredded.
HIPAA breach exceptions
There are also three main exceptions to the definition of “breach” in the rule.
1. A staff member (or someone acting under the direction) of a covered entity or business associate acquires, accesses, or uses PHI unintentionally. This counts as an exception as long as they came in contact with the PHI in good faith and within the scope of their role.
Example: A colleague accidentally opens the wrong hard copy file and sees the PHI of one of your clients.
2. A staff member of a covered entity or business associate discloses PHI to another staff member in the same organization or within an organized healthcare arrangement, and both people are authorized to access the information.
Example: You accidentally share a client’s name when talking to a colleague in the same practice.
3. A staff member of a covered entity or business associate shares information with someone who isn’t authorized to see or use it, but they have good reason to believe it won’t be retained.
Example: You are ready to leave the office when you notice a client sign-in sheet on the reception desk. You are about to put it away when a cleaning employee walks by the desk and glances at the sheet. Although the cleaner is not authorized to see the PHI, you have good reason to believe they won’t retain the information.
Incidental disclosures
The Privacy Rule also makes exceptions for incidental disclosures. These are mini-disclosures that can happen when you work in healthcare but are unavoidable and unlikely to cause any significant harm.
How do you tell if an event is an incidental disclosure? It is:

- Secondary (it happens as the result of another disclosure allowed by the Privacy Rule)
- Unavoidable (there’s no way to prevent it)
- Limited (only small amounts of information are revealed)
For example, if a client walks past an office in a mental health clinic and overhears parts of a therapy session, it may not be considered a breach if it meets the criteria of an incidental disclosure.
- It’s secondary. The information the client hears in the hallway results from an allowed disclosure (another client talking to their therapist).
- It’s unavoidable. Even though the door is closed and the room is sound-proofed, there’s nothing else the practice can do to ensure voices aren’t heard from the hallway.
- It’s limited. The client in the hallway can’t hear the whole conversation and doesn’t know the name of the client in the room.
Incidental disclosures apply as long as you have reasonable safeguards in place to protect PHI, according to the Privacy Rule. These include:
- Locking file cabinets
- Using strong passwords on your computers and changing them regularly
- Keeping computer monitors shielded from the public
- Ensuring computer screens lock after a period of inactivity
Low risk breaches
The Breach Notification Rule also makes allowances for breaches that are proven to have a low probability of compromising PHI based on a risk assessment. If you complete a risk assessment and have good reason to believe the breach is low risk, it may not be necessary to report it.
This risk assessment is optional, according to the HHS. If you would rather report the breach without doing a risk assessment, that’s fine.
You can complete a risk assessment by answering the following questions:
- What kind of information was compromised?
- How much information was accessed?
- How were individuals identified? How likely is it that sensitive information could be traced back to them?
- Who saw, accessed, or used the information?
- Was the PHI actually obtained or viewed?
- How has the risk to the PHI been mitigated?
For example, let’s say a mental health clinic accidentally emailed a client, Jane Torres, a spreadsheet with PHI. Jane deleted it right away and informed the clinic. The spreadsheet contained a list of clients in the clinic diagnosed with depression. However, each client was identified by a number, not a name. The spreadsheet didn’t contain any client addresses, phone numbers, or other identifying information.
This situation could be classified as being a low risk to the privacy and security of the PHI. Jane Torres is a well-known client of the clinic, not a hacker. She deleted the email right away. And since each client was identified only by numbers, even if Jane did peek at the spreadsheet, she would have had no way to match the information in it with actual people.
However, it’s always best to approach a situation like this with extreme caution. Incorrectly deciding a breach is low risk and failing to report it could lead to an HHS investigation and other consequences.
When in doubt, make the required notifications.
How to notify individuals affected by a breach

In addition to defining what a breach is, the Breach Notification Rule describes whom to notify when a breach happens and how.
It’s vital to follow this process carefully. If you wait too long to report a breach or fail to document the actions you took, you are violating HIPAA.
According to the rule, you must notify the individuals affected, the HHS, and in some cases, the media. This is in addition to other steps you should take to make sure the breach is contained.
A breach may happen at your practice or may be reported to you by a Business Associate you’re working with. If the Business Associate experiences the breach, they must provide you with all the relevant details (e.g., what happened, the number of people affected, their names, etc.). You are then required to make the necessary notifications.
How and when to notify individuals of a breach
According to the Breach Notification Rule, you must notify individuals affected by the breach either by first-class mail to their last known address or by email, if they have given permission to be contacted this way.
You have 60 days after discovering a breach to report it to the people involved. The only exception to this is if a law enforcement official tells you verbally or in writing that providing this notification would impede an investigation or compromise national security.
If you are missing an email or physical address for fewer than 10 people, you may inform them of the breach by phone, another form of written notice, or in another way.
If you are missing an email or physical address for 10 or more people, you must either:
- Post a conspicuous breach notification on the home page of your website for 90 days
OR
- Publish a conspicuous notice in major print or broadcast media in areas where the affected individuals likely live
For breaches affecting 500 people or more, you must inform prominent media outlets in your area in addition to sending individual notifications.
Don’t forget to include a toll-free phone number on all your notifications! The number must be active for at least 90 days.
If the situation is urgent, you may notify people by telephone first in addition to providing written notice.
What to include in a breach notification
In your notice to either individuals or the media, you should include:
- A short description of the breach
- The date of the breach
- The date you discovered it
- The types of information involved (e.g., names, addresses, dates of birth, social security numbers, etc.)
- How individuals may protect themselves from harm (some organizations provide free credit monitoring, for example)
- How you are investigating the breach
- Actions you are taking to reduce harm
- How you plan to prevent similar breaches in the future
- Contact information for your practice, including a toll-free phone number
When and how to notify the HHS of a breach
In addition to notifying individuals impacted by a breach, you must also inform the Secretary of HHS. You do this by completing a form on the HHS website.
The timeline for notifying the HHS depends on the number of people who were affected.

If 500 individuals or more are impacted by the breach, you must notify the Secretary without unreasonable delay and no more than 60 days after the breach is discovered.
For smaller breaches involving fewer than 500 people, you must notify the HHS annually and no later than 60 days after the end of the year. You don’t have to wait until year-end, though; you can notify the HHS earlier if you prefer.

HIPAA breach documentation
When a breach happens, it’s critical to keep good records. According to the Breach Notification Rule, Covered Entities and Business Associates carry the responsibility of proving they followed the regulations appropriately.
If you conduct a risk assessment of the breach, be sure to keep it on file. If you determine the breach is low risk, note how you arrive at that decision and keep copies of any emails or other related documents.
If you experience a breach, keep accurate and detailed notes on all the notifications you make and when. Retain significant emails and all other records.
Preparation is also key. If you don’t already have them, put written policies and procedures in place describing how you intend to follow the Breach Notification Rule in your practice. These should include:
- How you would investigate a breach
- Steps you would take to mitigate it
- How you would make the appropriate notifications
- How staff (if you have them) would be sanctioned for not following the rules
And if you have staff, don’t forget to train them on your policies!
How to prevent a HIPAA breach
Dealing with a breach is complicated. Aside from making the appropriate notifications, breaches can trigger investigations by the Office for Civil Rights (OCR) and may lead to a loss of reputation, income, or other consequences.
Stop breaches before they happen by following these steps:
- Safeguard PHI according to the HIPAA guidelines. Don’t know what these are? Download and study this guide.
- Make sure you have written policies and procedures on breaches in place
- If you have staff, train them on your policies
- Conduct a risk assessment at least once per year and after a breach
- Only use HIPAA-compliant service providers, like Hushmail, to handle e-PHI
HIPAA breach FAQs
What’s the difference between a HIPAA breach and a violation?
A breach means data has been compromised. A HIPAA violation happens when a Covered Entity or Business Associate has broken one or more of the HIPAA rules.
A HIPAA violation may lead to a breach, but breaches can happen even if the rules have been followed.
How does the breach notification rule apply to deceased clients?
If you know your client has passed away and you have address information for their next of kin or legal representative (an executor, for example) then notify that person.
Need HIPAA-compliant email? Check out Hushmail for Healthcare!
Overwhelmed by the business side of private practice? In this guide, therapists share 20 ways they've offloaded what drains them, to create more space for the work they love.




