Compliance
How to do your HIPAA risk assessment (with template)

Don’t forget that risk assessments are required for good reason. Protecting your clients’ health information is part of your professional responsibility to keep client information confidential.
Conducting regular risk assessments also helps protect your practice. Complaints of HIPAA (Health Insurance Portability and Accountability Act) violations and security breaches affect thousands of businesses every year. In 2021, the Office for Civil Rights (OCR) received over 34,000 complaints of alleged HIPAA infractions. In the same year, breaches affected over 37 million people. Risk assessments can help protect your business from complaints or security problems such as these, which can compromise your reputation and cost you valuable time and money.
Ultimately, HIPAA risk assessments are simply part of running an ethical and successful practice. And the good news is that once you become familiar with the process, it gets easier.
What is a HIPAA risk assessment?
First, let’s take a look at what a HIPAA risk assessment (also known as a risk analysis) is.
As you may know, HIPAA rules have two main categories — security and privacy. The privacy rule covers risks to the confidentiality, integrity and availability of protected health information (PHI) when it is not in electronic format, while the security rule governs electronic protected health information (e-PHI). In this article, we’ll focus on the security rule requirements only. However, it’s important to note that regular privacy rule assessments are also required.
According to the U.S. Department of Health and Human Services (HHS), a security risk assessment is “an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the [organization].”
In a nutshell, it involves taking stock of where your electronic client data is stored and how it could be compromised. You will need to consider threats in your office and online.
Is a HIPAA risk assessment necessary?
The short answer is yes. A risk assessment is an integral part of running a HIPAA-compliant practice. It constitutes part of your ethical responsibility to keep client information confidential. There are also important regulatory implications.
You may think of risk assessments as a way to create a safe space for client data. They help you maintain high professional standards by reducing the probability of your clients’ most sensitive information falling into the wrong hands.
Health practices that fail to comply with HIPAA rules by not doing regular risk assessments also face significant regulatory consequences.
In 2021, Peachstate Health Management in Georgia was fined $25,000 when an auditor discovered the company had failed to do a risk assessment, in addition to other issues.
Fines are not the only practice risk. Lapses in HIPAA compliance can also lead to increased oversight in the form of a corrective action plan.
Hushmail’s VP of Finance and Legal, Steven Youngman, said, “The corrective action plan means that practices are subject to monitoring and must provide HHS's OCR division evidence of their compliance for two or three years. It is a significant administrative burden to be able to show HHS that the practice is doing what HIPAA requires.”
|
If your practice suffers a security breach affecting 500 or more individuals, it will face an investigation and appear on the HIPAA Wall of Shame. These consequences have the potential to significantly impact your business’s reputation.
What are HIPAA’s security risk assessment requirements?
The HIPAA security rule governs this process. It states that a security risk assessment must be completed, reviewed regularly, and documented. However, the rule leaves room for the owners or managers of healthcare practices to tailor the process to their unique needs.
How often should a HIPAA security risk assessment be performed?
The security rule states that healthcare providers should conduct risk assessments as needed.
Youngman advised, “The risk assessment should be done at least annually; it helps bring a consideration of risks to the forefront.”
|
The HHS also indicates that you should complete risk assessments after significant changes to computer equipment, services, or personnel.
Examples of changes that would trigger an assessment may include using a new computer system, hiring staff, bringing on new practice partners, or changing your electronic health records (EHR) provider.
How to document your risk assessment
Again, practices have some leeway here to document the risk assessment in whatever way suits their needs.
“Electronic copies are fine, as long as they are saved, including supporting notes,” said Youngman. “If necessary, the organization may need to prove how their risk assessment evolved over time and to show that they were compliant.”
|
 Step 1: Prepare your practice and create an inventory for your HIPAA security risk assessment
Step 1: Prepare your practice and create an inventory for your HIPAA security risk assessment
Preparing for an assessment before diving in will help speed up the process and make it easier. It can also help reduce overwhelm.
It often helps to have one person in a practice become familiar with the HIPAA regulations, gather all the necessary information and conduct the assessment (with oversight). If you are running a solo practice, this task falls on you. If you have staff members, you may consider delegating some of these responsibilities to one of them.
You’ll also need to book a meeting with any staff members to discuss what is involved in the process and begin gathering information.
If you don’t have staff, block some time in your calendar to work on the assessment. Consider booking an hour per week for the next four weeks. This is only an estimate; the assessment could take more or less time.
Inventory
Make a list of the people, businesses, and equipment involved with your electronic information using the categories listed below. You’ll find space for this in our Security Risk Assessment Template.
Make lists of:
- Computer equipment and where it’s physically located. Include desktop and laptop computers with patient data, portable external hard drives, etc.
- Staff (if any) with access to electronic files
- Third-party provider Business Associates (EHR, email, cloud-based data storage, teletherapy, etc.)
Step 2: Identify Threats
Now consider potential threats to your client data. Review the lists you made in Step 1 and consider how a threat or vulnerability could compromise each category (computer equipment, staff, third-party providers). Note the threats you come up with.
- If you store client information on a laptop, for example, it could be stolen from your office or car.
- Any information transmitted online could be hacked.
- If you have a staff member with access to client information, consider what could happen if a password were written down and left sitting on a desk.
- Could a former staff member access your client files?
- Do you have a process to wipe your computer’s hard drive before recycling it?
Be sure to include all physical threats to e-PHI, such as natural disasters or break-ins.
Make sure all your third-party providers are HIPAA compliant and that you have Business Associate Agreements (BAAs) in place.
As you identify potential problems, note any policies and procedures you already follow. These could include setting computer screens to lock when unattended, updating passwords regularly, securing your office door, and more.
These are a few ideas to get you started, not an exhaustive list. Go through each item and carefully consider the unique threats or vulnerabilities your practice faces.
Step 3: Prioritize threats
Once you have identified how your e-PHI could be compromised, the next step is determining which threats are most likely and pose the highest risk.
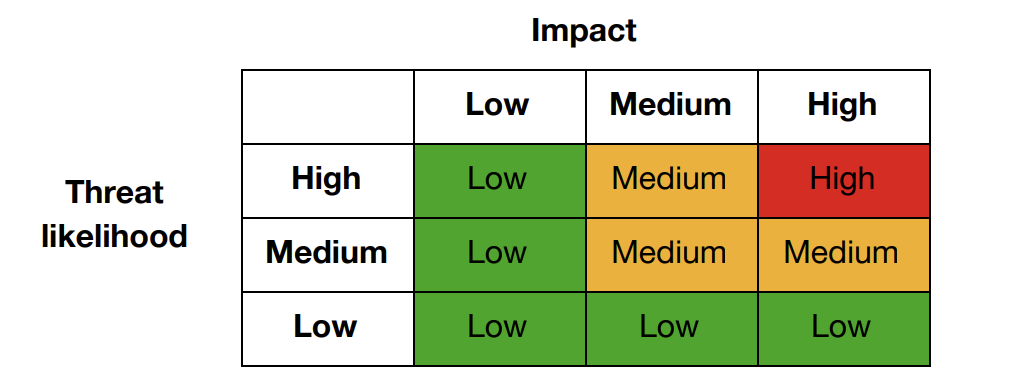
This risk level matrix can help you assess both the likelihood of a specific risk and its significance.
For each threat or vulnerability identified, determine whether its likelihood is low, medium, or high, then consider its impact on your practice using the same scale.
Next, use the matrix to determine a threat’s overall risk level (low, medium, or high). The likelihood of a threat is shown on the vertical axis and its impact on the horizontal.
Finally, write the overall score (low, medium, high) next to the threat.
Step 4: Fix priority issues
Once you have prioritized threats to e-PHI, deciding which ones to deal with first is easy. Plan to remedy high-risk threats immediately, then tackle medium-level issues. Low-level concerns may be addressed last.
If you have staff members, meet to review the problems you found and make a plan for dealing with them. If not, make yourself a to-do list with deadlines, then add the tasks to your agenda.
You may need to switch from a third-party provider that isn’t HIPAA compliant to one that is — like Hushmail. Depending on the needs of your practice, you may also consider putting procedures in place to effectively destroy client data before replacing computer equipment.
There are also simpler fixes like setting reminders to change passwords regularly or turning on two-step verification. Of course, the steps you take will depend on your practice’s requirements.
Resources
In addition to our helpful template, several other resources may assist you in completing your security risk assessment.
Here are some useful tools:
- The HHS website offers guidance on the HIPAA rules and risk analysis process.
- HHS has also created a Security Risk Assessment Tool. It can be downloaded to computers using Microsoft Windows 7, 8, 10, or 11. An Excel workbook is also available for those without Microsoft Windows or who want to customize the tool.
- The “Security Standards: Implementation for the Small Provider” guide contains excellent information for smaller practices.
- The National Institute of Standards and Technology (NIST) Guide for Conducting Risk Assessments may also be helpful.
Takeaway
In this article, we have covered what HIPAA risk assessments are and how to do one.
It’s ideal to complete a risk assessment every year or when making changes to your practice, computer equipment or the services you use.
Failure to complete an assessment can have significant consequences, including increased oversight or weighty fines. It can also result in loss of reputation and income if complaints become public.
Remember, the energy you put into your risk assessment benefits you and your practice. It can give you valuable information about the equipment and systems you use. You’ll also gain peace of mind, knowing you have done everything you can to keep your clients’ health information safe.




