5 tips to strengthen the cybersecurity of your virtual office
-1.jpg?noresize&width=800&name=Untitled%20design(1)-1.jpg)
-1.jpg?width=1920&name=Untitled%20design(1)-1.jpg)
Last week we wrote about risk assessment as a way of strengthening the security of your virtual office. This week we’re providing five actionable tips to help strengthen your practice’s cybersecurity even more. Even if you’re well-versed in security best practices, things have changed so much in the last six months; you might want to take another look at what you’re doing to keep your clients’ information safe. National Cybersecurity Awareness Month is a perfect time to make these five important security checks.
1. Make sure you’re using telehealth in a secure manner
When you first went virtual with your practice during the shutdown, it might have been tempting to default to whatever video platform you were already familiar with. The fact that HIPAA regulations were loosened made it easy to make the quickest, but possibly not the most secure decision.
Data security matters to nearly a majority of Americans considering telehealth options for mental health. Consider this recent article from Business Wire:
Amid rising mental health struggles for many during the COVID-19 pandemic, a survey from leading healthcare cybersecurity firm CynergisTek reveals that nearly a majority of Americans (46 percent) would embrace telehealth widely for mental health and therapy sessions, but worry most about their behavioral health data being exposed by hackers.
Now is a good time to check to see if your provider is secure and HIPAA compliant by asking for a signed Business Associate Agreement (BAA). Although some platforms may hint at HIPAA compliance, a BAA is a signed document affirming that the service accepts responsibility for the security of your clients’ data.
Our partner Person Centered Tech reviews 15 different video conference products on their website and clearly notes the ones they recommend for your HIPAA risk management needs. Being able to reassure prospective clients that their data will be safe could be that added peace of mind they need to choose your practice for their care.
Make sure your clients are using teletherapy securely as well
It’s also important to ensure that your clients are informed about how to use telehealth securely on their end. Here is a helpful infographic from our friends at Theranest that you can give to your clients to help them prepare.
We recently profiled Carol Park, LPC-S, RD, who uses a Technology Consent to Treatment addendum to her regular Consent to Treatment form to ensure her clients have the information they need and understand any risks associated with teletherapy.
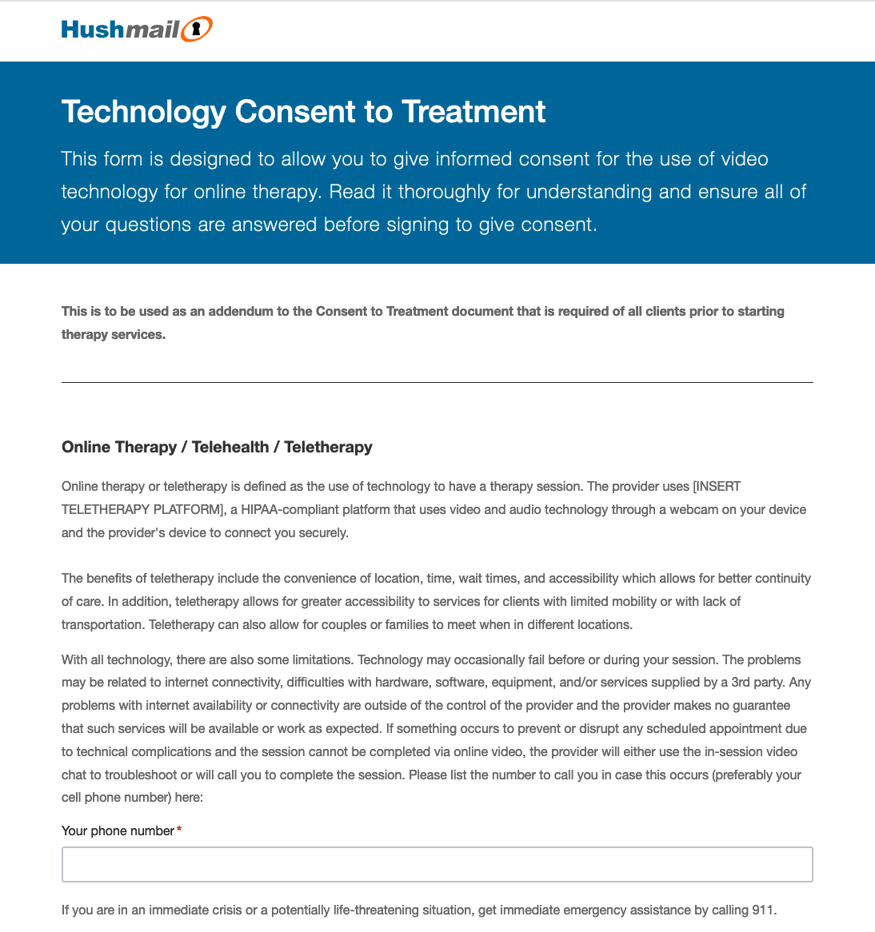
View complete form. This form is modeled on the Technology Consent to Treatment Carol Park, LPC-S, RD, uses in her practice. If you would like to use this form, let Hushmail know, and we’ll be happy to duplicate it in your account, subject to the number of forms allowed on your plan.
2. Secure your home office computer and workspace
Now that you’re working from home on a consistent basis, you might be experiencing issues that weren’t immediately evident. For example, you might find yourself bargaining for valuable office real-estate in your home or needing to increase the security of your technology.
Working from home involves unique security and privacy challenges. Here are a few things you’ll want to consider:
A designated work computer. Providing behavioral health services to clients isn’t an occupation that lends itself to using the family computer in the nook next to the kitchen. Make sure that you have a computer of your own that’s password protected and updated regularly with reliable anti-virus protection software.
A designated work space that provides privacy during teletherapy sessions. Your clients’ conversations must remain private. Consider how someone might overhear a session. Privacy might require certain physical safeguards such as double-paned windows and doors that lock securely. Set up your office so your online sessions are just as private as they would be in person.
A secure wireless connection. Even if you plug straight into your modem for your teletherapy sessions, a secure wireless connection is still necessary to protect your clients’ information. Wi-Fi that’s not secure could allow hackers to access client files on your computer. Securing your password starts with a strong, unique password, but there are other measures you can take to keep hackers from breaking in. This helpful FTC article from the Federal Trade Commission about how to secure your Wi-Fi will help you make sure your wireless network is as secure as possible.
3. Use strong, unique passwords for all of your accounts
Speaking of strong, unique passwords, good password practices apply to all of your accounts, not just your Wi-Fi. The National Cyber Security Alliance advises that you “avoid using common words in your passwords. Substitute letters with numbers and punctuation marks or symbols. For example, @ can replace the letter “A” and an exclamation point (!) can replace the letters “I” or “L,” and that the best way to store your passwords is to “utilize a password manager to remember all your long passwords.” For more password tips from the National Cyber Security Alliance, read their article Creating a password.
Whatever you do, be sure to use unique and strong passwords for all of your accounts. That way, if one account is hacked, the damage is limited to that account.
4. Enable two-step verification
Also called two-factor authentication, two-step verification is an extra layer of protection that you can put in place for many of your accounts. It requires you to verify your identity using two different methods when signing in to an account from a new computer or device. Not all services offer two-step verification, but it’s worth finding out if they do.
Accounts that you might want to protect with two-step verification include email accounts, your EHR or other practice management service, and any cloud-based service that stores client or practice information. You can easily turn it on for your Hushmail account by going to your account settings. Our recent blog post 4 security measures you might not be taking, but maybe you should walks you through the steps.
5. Make sure your BAAs are in order
As mentioned earlier in this post, many services claim that they’re secure. However, unless they provide you with a signed BAA, you can’t in good faith claim to your clients that their data is protected when you use the service.
And if you undergo a HIPAA audit, unless you have that BAA, you won’t have the documentation you need to affirm that your third-party service is keeping your clients’ data secure.
The purpose of a BAA is simple. When you subscribe to a service, such as an email service, EHR, or teletherapy platform, they need to protect your clients’ data if they’ll be handling it at any time. A BAA affirms that the service has put security safeguards in place and is willing to accept responsibility for the safety of your clients’ information.
Need a HIPAA-compliant email, web form, and e-signature service that comes with a BAA?
|
National Cybersecurity Awareness Month is a perfect time to make these five important security checks: 1) make sure you’re using telehealth in a secure manner; 2) secure your home office computer and workspace; 3) use strong, unique passwords for all of your accounts; 4) enable two-step verification; and 5) make sure your BAAs are in order. Related posts: |
Overwhelmed by the business side of private practice? In this guide, therapists share 20 ways they've offloaded what drains them, to create more space for the work they love.




