
Have you ever received an email from an organization, your bank perhaps, that looked just like the emails you usually receive, except this one instructed you to click on a link to handle an urgent matter? The email was well written, and the sender’s address looked like your bank’s address; it would be understandable if you had clicked on the link as requested. But hopefully, you didn’t, unless you verified that the email was from the assumed sender. That’s because this email was quite possibly a phishing email scam, which is commonly implemented through spoofing.
Email spoofing is the act of impersonating a person or institution through their email and is an increasing problem for anyone who uses email to communicate. It’s easy to do and often goes undetected. Fortunately, it’s not hard to detect when you know what you’re looking for, and there are easy ways to protect your domain from being spoofed. Understanding how spoofing works is the first step.
What is spoofing?
Spoofing is the fabrication of an email header and content for the purpose of tricking the recipient into thinking the email originated from an email address that’s not owned by the person sending the email. There are numerous reasons why someone might want to spoof an email:
- Phishing - tricking the recipient into giving personal information or access to accounts and other assets.
- To avoid the email recipient’s spam blacklist.
- To undermine a person’s reputation.
- To play a prank.
- To hide the sender’s true identity. This isn’t necessarily done for fraudulent purposes. However, there are much easier ways to achieve anonymity, such as using aliases.
How spoofing works
Email programs use Simple Mail Transfer Protocol (SMTP) to communicate with one another. This process announces to the receiving email server who you are and who you’re sending the email to. SMTP then writes the email contents to the server. Unfortunately, SMTP does nothing to verify that an email is actually from the entity it says it’s from.
Parts of an email
To understand spoofing, you must understand the parts of an email.
First, there’s the envelope. This is the part that’s usually invisible to both the sender and receiver. It contains important information about where the email’s from and where it’s going, as well as any records used for verification.
Here’s an example of what part of the email envelope might look like:
Return-Path: matthew.watson@hushmail.com
Received: from mip.hushmail.com (LHLO smtp5.hushmail.com) (65.39.178.78) by
server with LMTP; Mon, 5 Aug 2019 20:55:05 +0000 (UTC)
Received: from smtp5.hushmail.com (localhost [127.0.0.1])
by smtp5.hushmail.com (Postfix) with SMTP id E7A5920E51
for <raymond.rogers@hushmail.com>; Mon, 5 Aug 2019 20:55:04 +0000 (UTC)
Although it might not be immediately evident to the untrained eye, the sender in this example is matthew.watson@hushmail.com and the receiver is raymond.rogers@hushmail.com.
Next, you have the visible email header. This is what you usually see when you read your mail. It includes a “from” header that says who the email is from, as well as a “to” header and other headers depending on the email program. You can see it’s much easier to read than the envelope.
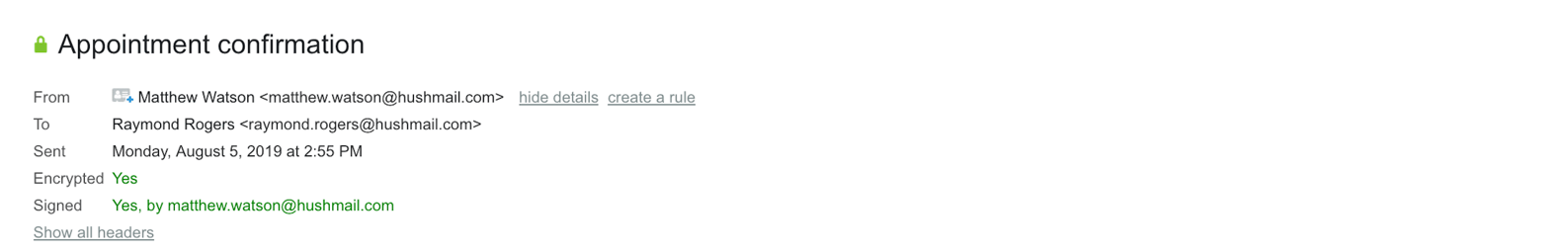
Lastly, you have the email body and any attachments.
How spoofing is accomplished
A person with a little tech-savvy can easily input any email address they wish into the visible “from” header by typing a little PHP code or a UNIX command. Someone with no tech knowledge can find a website that allows them to send fake emails. In other words, spoofing is a very easy thing to accomplish.
The visible “from” header can be any address the sender chooses and doesn’t have to reflect the sender’s real address (i.e., the one on the envelope). This makes it appear that the email is coming from someone it isn’t. The recipient could see this if they checked the visible header against the envelope header, but they normally don’t think to do this unless they’re suspicious. Because spoofing attempts often accurately mirror a legitimate email from a known sender, recipients can easily be fooled.
Another form of spoofing can be achieved by slightly misspelling a domain. For example, instead of paypal.com, the spoofer might use paypall.com. This type of spoofing is difficult to detect unless you’re paying attention to spelling because the misspelled address that’s visible to the recipient is the same as the sending domain and the address on the envelope. Therefore, the verifications discussed below aren’t much help. It’s crucial that you pay attention to spelling and catch errors that can alert you to a spoofing attempt.
What you can do to protect yourself and your domain
Spoofing is becoming more and more common and sophisticated; it’s come a long way from badly composed requests for large sums of money. Fortunately, it’s not impossible to detect a spoofed email or prevent your domain from being spoofed.
Let’s look at a few strategies you might have heard about and consider how they apply to spoofing.
Setting up your SPF (Sender Policy Framework) records is something we’ve written about a few times in our blog. Setting an SPF record for your email provider helps receiving servers reduce spam to their system by verifying that the sender is allowed to send email on the domain’s behalf. However, verification through SPF records doesn’t work on its own to flag spoofing attempts because it doesn’t check the visible “from” header, only the information on the envelope.
DKIM (Domain Key Identified Mail) is another strategy for protecting against spam that involves a signing process that authenticates an email at different points along its path. It’s a pretty complicated process, and we won’t go into the details here. Suffice to say that it doesn’t work on its own to flag spoofing attempts because, like verifying for SPF records, it doesn’t check the visible header.
DMARC (Domain-Based Message Authentication, Reporting, and Conformance) is a strategy that works by using the other two strategies. By using SPF authentication and DKIM authentication, DMARC checks and verifies that the visible “from” header matches the invisible “from” on the envelope. It can be used to protect your domain from being spoofed and it can also help you filter out spoofing attempts that come your way.
Although DMARC is used on email domains such as Hushmail.com, Gmail.com, and Outlook.com, DMARC is not used by most small business domains, because these domains are usually provided by a company other than the email provider. Unless the domain owner chooses to set up DMARC, it will most likely go without.
On the receiving end, many email providers use DMARC to verify incoming email messages, but not all. It’s best to check with your email provider to know if your incoming emails are being filtered in this way.
What you can do to prevent your email from being spoofed
Rely on DMARC
If you use one of our shared domains, such as @hushmail.com or @therapysecure.com, your account is protected with DMARC from people trying to spoof your email address.
However, if you’re using your own domain with your Hushmail account, you’ll need to set up DMARC. Contact us, and we’ll be happy to help you do this.
What you can do to detect an email that has been spoofed
Be wary of requests for sensitive information
A savvy cyber criminal can find all types of information about you and your colleagues. Even if an email seems to be appropriate for your situation (the sender is aware that you’ve been traveling, for example) don’t immediately assume the email’s legitimate. The best thing to do before handing over sensitive information is to confirm by phone, message, or a separate email (not a reply to the email in question).
Check the headers if you’re suspicious
If an email is urging you to complete an action that involves wiring money or inputting sensitive information or credentials, stop and check that the envelope “from” and header “from” match. In Hushmail’s webmail, all you have to do is click on Show all headers. Here is a helpful page that explains how to access the envelope information using other email programs.
If the headers don’t match, that doesn’t automatically mean the email’s been spoofed. There may be a legitimate reason within an organization to change the visible “from” header. Contact the sender to verify the email’s authenticity.
Check the spelling
Remember, spoofing attempts that use misspelled domain names will not be caught by DMARC because the envelope “from” matches the header “from.” Again, if you have any suspicion about an email, verify that the sending email address is spelled correctly.
Rely on DMARC
DMARC can help you both ways – protecting your domain from being spoofed and thwarting spoofing scams that come your way. If you have a Hushmail account, we automatically check that the emails you receive pass DMARC and send spoofing attempts to your spam folder.
Need a secure email that’s protected with DMARC?
Sign up for a Hushmail account, today. If you plan to use your own domain with one of our business accounts (including Hushmail for Healthcare), let us know if you’d like us to help you set up DMARC.

|
Email spoofing is the act of impersonating a person or institution through their email and is an increasing problem for anyone who uses email to communicate. It’s easy to do and often goes undetected. Fortunately, it’s not hard to detect when you know what you’re looking for, and there are easy ways to protect your domain from being spoofed. Understanding how spoofing works is the first step.
Related posts:
|